MSSPs can help their clients reduce risk and make better decisions after an alert by offering them an Endpoint Triage service. Endpoint Triage investigations are fast and show the scope of an attack, allowing your clients to more confidently decide between wiping and calling an IR team.
Endpoint Triage can be provided by internal MSSP teams or in partnership with external providers.
Making decisions after an alert can be stressful and clients will value that their MSSP provided them with an affordable option to reduce risk.
What is Endpoint Triage?
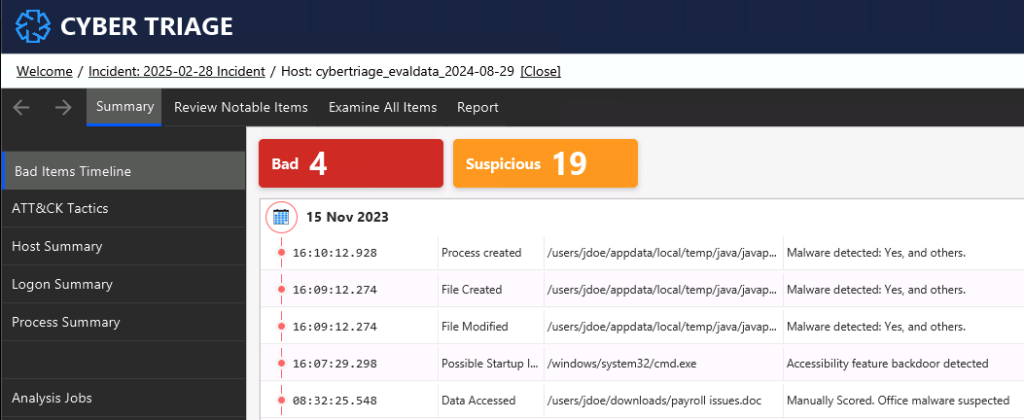
Endpoint Triage is a quick investigation of a host to determine if it has signs of a compromise and needs a deeper dive investigation. It is often done after an alert to decide what to do next:
Wipe the system or escalate to an IR team.
It answers basic questions like:
- Was data exfiltrated?
- Is there remote access?
- Were other hosts involved?
These questions allow for better decision-making and risk mitigation.
Clients Can’t Decide Based On A Single Alert
When clients are notified about an alert, they must make a hard decision about the next step:
| Decision | Impact If Wrong |
| Ignore It – Do Nothing | Attacker could persist and cause more damage. |
| Wipe It | Attacker could be persisting on other hosts and cause more damage. |
| Call an IR Team – Use Cyber Insurance | Pay the deductible for nothing. Next year’s premium will go up. |
Endpoint Triage is a middle ground between hoping for the best and invoking a full IR team.
The core problem is the initial alert doesn’t give them enough information to make the decision. The attacker could have been active for days before they triggered an alert. Mandiant reported their average time between when the attack started and first detection was 11 days.
Your clients can’t make decisions based only on a single alert. You can offer endpoint triage as an additional service to help them decide.
How To Provide Endpoint Triage
MSSPs can provide endpoint triage using both internal or external resources.
Build an In-House Team
Specialized investigation tools exist to make endpoint triage fast and effective. The key is being able to collect data and have it automatically analyzed.
Our Cyber Triage solution is agentless and is the leader in scoring of forensic artifacts. It has been optimized to look for endpoint triage topics, such as data exfiltration and lateral movement.
Use an External Team
External DFIR teams can sometimes provide this service. When purchasing this, consider some companies have a minimum deal size bigger than a single endpoint triage.
Our Rapid Endpoint Triage service is fixed price and allows you to upload data from the endpoint directly to our servers and our team will analyze the results.

Endpoint Triage Helps Clients
No one wants to make the wrong decision when faced with an alert. Endpoint triage makes that decision-making easier.
The easiest way to start offering this service and test demand is to outsource it to a 3rd party and offer it as an add-on. As the demand increases, consider training your team and bundling it with your contracts.
For more information:
